Computer Network GATE previous year questions with answer
Ques 1 Gate 2024 Set-1
A user starts browsing a webpage hosted at a remote server. The browser opens a
single TCP connection to fetch the entire webpage from the server. The webpage
consists of a top-level index page with multiple embedded image objects. Assume
that all caches (e.g., DNS cache, browser cache) are all initially empty. The
following packets leave the user’s computer in some order.
(i) HTTP GET request for the index page
(ii) DNS request to resolve the web server’s name to its IP address
(iii) HTTP GET request for an image object
(iv) TCP SYN to open a connection to the web server
Which one of the following is the CORRECT chronological order (earliest in time
to latest) of the packets leaving the computer ?
Ques 2 Gate 2022
Consider an enterprise network with two Ethernet segments, a web server and a firewall, connected via three routers as shown below.
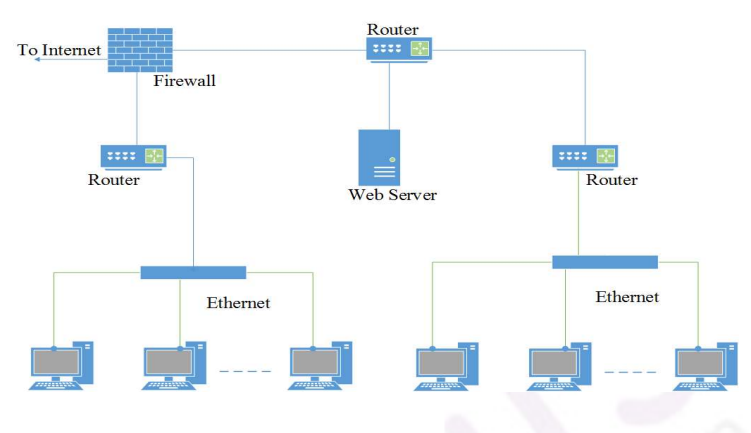
What is the number of subnets inside the enterprise network?
Ques 3 Gate 2022
Consider a network with three routers P, Q, R shown in the figure below. All the links have cost of unity.
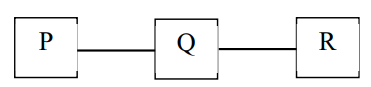
The routers exchange distance vector routing information and have converged on the routing tables, after which the link Q−R fails. Assume that P and Q send out routing updates at random times, each at the same average rate. The probability of a routing loop formation (rounded off to one decimal place) between P and Q, leading to count-to-infinity problem, is___________
Ques 4 Gate 2022
Consider the data transfer using TCP over a 1 Gbps link. Assuming that the maximum segment lifetime (MSL) is set to 60 seconds, the minimum number of bits required for the sequence number field of the TCP header, to prevent the sequence number space from wrapping around during the MSL is____________.
Ques 5 Gate 2022
Consider a 100 Mbps link between an earth station (sender) and a satellite (receiver) at an altitude of 2100 km. The signal propagates at a speed of 3x108 m/s. The time taken (in milliseconds, rounded off to two decimal places) for the receiver to completely receive a packet of 1000 bytes transmitted by the sender is_________.
Ques 6 Gate 2022
Consider the resolution of the domain name www.gate.org.in by a DNS resolver. Assume that no resource records are cached anywhere across the DNS servers and that an iterative query mechanism is used in the resolution. The number of DNS query-response pairs involved in completely resolving the domain name is________.
Ques 7 Gate 2020
Consider the following statements about the functionality of an IP based router.
I. A router does not modify the IP packets during forwarding.
II. It is not necessary for a router to implement any routing protocol.
III. A router should reassemble IP fragments if the MTU of the outgoing link is larger than the size of the incoming IP packet.
Which of the above statements is/are TRUE ?
Ques 8 Gate 2020
Consider a TCP connection between a client and a server with the following specifications; the round trip time is 6 ms, the size of the receiver advertised window is 50 KB, slow-start threshold at the client is 32 KB, and the maximum segment size is 2 KB. The connection is established at time t=0. Assume that there are no timeouts and errors during transmission. Then the size of the congestion window (in KB) at time t+60 ms after all acknowledgements are processed is _________ .
Ques 9 Gate 2020
Assume that you have made a request for a web page through your web browser to a web server. Initially the browser cache is empty. Further, the browser is configured to send HTTP requests in non-persistent mode. The web page contains text and five very small images. The minimum number of TCP connections required to display the web page completely in your browser is ________ .
Ques 10 Gate 2019
Consider that 15 machines need to be connected in a LAN using 8-port Ethernet switches. Assume that these switches do not have any separate up link ports. The minimum number of switches needed is ___________.

Total Unique Visitors