CS/IT Gate Yearwise
CS/IT Gate 2025 (Set 2)
CS/IT Gate 2024 (Set 1)
CS/IT Gate 2024 (Set 2)
CS/IT Gate 2023
CS/IT Gate 2022
CS/IT Gate 2021 (Set 1)
CS/IT Gate 2021 (Set 2)
CS/IT Gate 2020
CS/IT Gate 2019
CS/IT Gate 2018
CS/IT Gate 2017 (Set 1)
CS/IT Gate 2017 (Set 2)
CS/IT Gate 2016 (Set 1)
CS/IT Gate 2016 (Set 2)
CS/IT Gate 2015 (Set 1)
CS/IT Gate 2015 (Set 2)
CS/IT Gate 2015 (Set 3)
CS/IT Gate 2014 (Set 1)
CS/IT Gate 2014 (Set 2)
CS/IT Gate 2014 (Set 3)
CS and IT Gate 2024 Set-1 Questions with Answer
Ques 40 GATE 2024 SET-1
Let A be an n × m matrix with m > n. Which of the following statements is/are TRUE about the system Ax = 0?
Ques 41 GATE 2024 SET-1
Consider the 5-state DFA M accepting the language L(M) ⊂ (0 + 1)* shown below. For any string w ∈ (0 + 1)* let n0(w) be the number of 0′s in w and n1(w) be the number of 1′s in w.
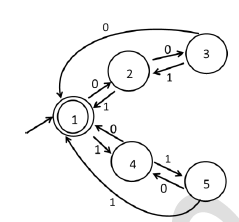
Ques 42 GATE 2024 SET-1
The chromatic number of a graph is the minimum number of colours used in a proper colouring of the graph. Let G be any graph with n vertices and chromatic number k. Which of the following statements is/are always TRUE?
Ques 43 GATE 2024 SET-1
Consider the operators ◊ and □ defined by a ◊ b = a + 2b, a □ b = ab. for positive integers. Which of the following statements is/are TRUE?
Ques 44 GATE 2024 SET-1
Consider two set-associative cache memory architectures: WBC, which uses the write back policy, and WTC, which uses the write through policy. Both of them use the LRU (Least Recently Used) block replacement policy. The cache memory is connected to the main memory. Which of the following statements is/are TRUE?
Ques 45 GATE 2024 SET-1
Consider a 512 GB hard disk with 32 storage surfaces. There are 4096 sectors per track and each sector holds 1024 bytes of data. The number of cylinders in the hard disk is
Ques 46 GATE 2024 SET-1
The baseline execution time of a program on a 2 GHz single core machine is 100 nanoseconds (ns). The code corresponding to 90% of the execution time can be fully parallelized. The overhead for using an additional core is 10 ns when running on a multicore system. Assume that all cores in the multicore system run their share of the parallelized code for an equal amount of time. The number of cores that minimize the execution time of the program is
Ques 47 GATE 2024 SET-1
A given program has 25% load/store instructions. Suppose the ideal CPI (cycles per instruction) without any memory stalls is 2. The program exhibits 2% miss rate on instruction cache and 8% miss rate on data cache. The miss penalty is 100 cycles. The speedup (rounded off to two decimal places) achieved with a perfect cache (i.e., with NO data or instruction cache misses) is
Ques 48 GATE 2024 SET-1
Consider the following code snippet using the fork() and wait() system calls. Assume that the code compiles and runs correctly, and that the system calls run successfully without any errors.
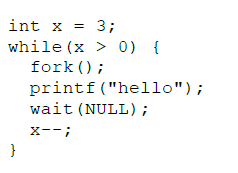
Ques 49 GATE 2024 SET-1
Consider the entries shown below in the forwarding table of an IP router. Each entry consists of an IP prefix and the corresponding next hop router for packets whose destination IP address matches the prefix. The notation "/N" in a prefix indicates a subnet mask with the most significant N bits set to 1.
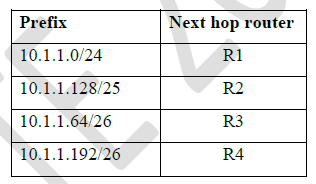
Ques 50 GATE 2024 SET-1
Let G = (V, Σ, S, P) be a context-free grammar in Chomsky Normal Form with Σ = {a, b, c} and V containing 10 variable symbols including the start symbol S. The string w = a30 b30 c30 is derivable from S. The number of steps (application of rules) in the derivation S →* w is
Ques 51 GATE 2024 SET-1
The number of edges present in the forest generated by the DFS traversal of an undirected graph G with 100 vertices is 40. The number of connected components in G is
Ques 52 GATE 2024 SET-1
A bag contains 5 red balls and 7 green balls. Two balls are drawn randomly without replacement. If it is known that the first ball drawn is red, the probability (rounded off to two decimal places) that both balls drawn are red is____________.

Total Unique Visitors