CS/IT Gate Yearwise
CS/IT Gate 2025 (Set 2)
CS/IT Gate 2024 (Set 1)
CS/IT Gate 2024 (Set 2)
CS/IT Gate 2023
CS/IT Gate 2022
CS/IT Gate 2021 (Set 1)
CS/IT Gate 2021 (Set 2)
CS/IT Gate 2020
CS/IT Gate 2019
CS/IT Gate 2018
CS/IT Gate 2017 (Set 1)
CS/IT Gate 2017 (Set 2)
CS/IT Gate 2016 (Set 1)
CS/IT Gate 2016 (Set 2)
CS/IT Gate 2015 (Set 1)
CS/IT Gate 2015 (Set 2)
CS/IT Gate 2015 (Set 3)
CS/IT Gate 2014 (Set 1)
CS/IT Gate 2014 (Set 2)
CS/IT Gate 2014 (Set 3)
CS and IT Gate 2023 Questions with Answer
Ques 14 GATE 2023
The Lucas sequence Ln is defined by the recurrence relation:
Ln = Ln-1 + Ln-2, for n ≥ 3, with L1 = 1 and L2 = 3.
Which one of the options given is TRUE?
Ques 15 GATE 2023
Suppose two hosts are connected by a point-to-point link and they are configured to use Stop-and-Wait protocol for reliable data transfer. Identify in which one of the following scenarios, the utilization of the link is the lowest.
Ques 16 GATE 2023
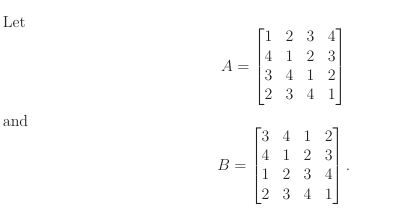
Ques 17 GATE 2023
Consider the following definition of a lexical token id for an identifier in a programming language, using extended regular expressions:

Ques 18 GATE 2023
An algorithm has to store several keys generated by an adversary in a hash table. The adversary is malicious who tries to maximize the number of collisions. Let k be the number of keys, m be the number of slots in the hash table, and k > m. Which one of the following is the best hashing strategy to counteract the adversary?
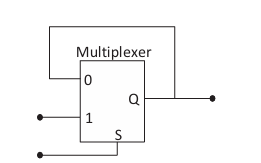
Ques 19 GATE 2023
The output of a 2-input multiplexer is connected back to one of its inputs as shown in the figure.
Ques 20 GATE 2023
Which one or more of the following need to be saved on a context switch from one thread (T1) of a process to another thread (T2) of the same process?
Ques 21 GATE 2023
Which one or more of the following options guarantee that a computer system will transition from user mode to kernel mode?
Ques 22 GATE 2023
Which of the following statements is/are INCORRECT about the OSPF (Open Shortest Path First) routing protocol used in the Internet?
Ques 23 GATE 2023
Geetha has a conjecture about integers, which is of the form
∀x(P(x)⇒∃yQ(x,y)),
where P is a statement about integers, and Q is a statement about pairs of integers. Which of the following (one or more) option(s) would imply Geetha's conjecture?
Ques 24 GATE 2023
Let f(x) = x3 + 15x2 - 33x - 36 be a real-valued function. Which of the following statements is/are TRUE?
Ques 25 GATE 2023
Let f and g be functions of natural numbers given by f(n) = n and g(n) = n2. Which of the following statements is/are TRUE?
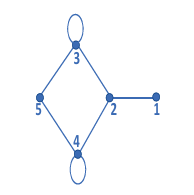
Ques 26 GATE 2023
Let A be the adjacency matrix of the graph with vertices {1, 2, 3, 4, 5}.

Total Unique Visitors