CS/IT Gate Yearwise
CS/IT Gate 2025 (Set 2)
CS/IT Gate 2024 (Set 1)
CS/IT Gate 2024 (Set 2)
CS/IT Gate 2023
CS/IT Gate 2022
CS/IT Gate 2021 (Set 1)
CS/IT Gate 2021 (Set 2)
CS/IT Gate 2020
CS/IT Gate 2019
CS/IT Gate 2018
CS/IT Gate 2017 (Set 1)
CS/IT Gate 2017 (Set 2)
CS/IT Gate 2016 (Set 1)
CS/IT Gate 2016 (Set 2)
CS/IT Gate 2015 (Set 1)
CS/IT Gate 2015 (Set 2)
CS/IT Gate 2015 (Set 3)
CS/IT Gate 2014 (Set 1)
CS/IT Gate 2014 (Set 2)
CS/IT Gate 2014 (Set 3)
CS and IT Gate 2014 Set-2 Questions with Answer
Ques 1 GATE 2014 SET-2
Consider two strings A = ""qpqrr"" and B = ""pqprqrp"". Let x be the length of the longest common subsequence (not necessarily contiguous) between A and B and let y be the number of such longest common subsequences between A and B. Then x + 10y = _______.
Ques 2 GATE 2014 SET-2
Suppose P, Q, R, S, T are sorted sequences having lengths 20, 24, 30, 35, 50 respectively. They are to be merged into a single sequence by merging together two sequences at a time. The number of comparisons that will be needed in the worst case by the optimal algorithm for doing this is _______.
Ques 3 Gate 2014 Set-2
The number of people diagnosed with dengue fever (contracted from the bite of a mosquito) in north India is twice the number diagnosed last year. Municipal authorities have concluded that measures to control the mosquito population have failed in this region. Which one of the following statements, if true, does not contradict this conclusion?
Ques 4 Gate 2014 Set-2
The old city of Koenigsberg, which had a German majority population before World War 2, is now called Kaliningrad. After the events of the war, Kaliningrad is now a Russian territory and has a predominantly Russian population. It is bordered by the Baltic Sea on the north and the countries of Poland to the south and west and Lithuania to the east respectively. Which of the statements below can be inferred from this passage?
Ques 5 Gate 2014 Set-2
Match the columns.
| Column 1 | Column 2 |
|---|---|
| 1) eradicate | P) misrepresent |
| 2) distort | Q) soak completely |
| 3) saturate | R) use |
| 4) utilize | S) destroy utterly |
Ques 6 Gate 2014 Set-2
Who _________ was coming to see us this evening?
Ques 7 Gate 2014 Set-2
Choose the most appropriate phrase from the options given below to complete the following sentence.
India is a post-colonial country because
Ques 8 Gate 2014 Set-2
If x is real and |x2 - 2x + 3| = 11, then possible values of |- x3 + x2 - x| include
Ques 9 GATE 2014 SET-2
Which one of the following is TRUE about the interior gateway routing protocols Routing Information Protocol (RIP) and Open Shortest Path First (OSPF)?
Ques 10 GATE 2014 SET-2
Which one of the following socket API functions converts an unconnected active TCP socket into a passive socket?
Ques 11 GATE 2014 SET-2
In the diagram shown below, L1 is an Ethernet LAN and L2 is a Token-Ring LAN. An IP packet originates from sender S and traverses to R, as shown. The links within each ISP and across the two ISPs, are all point-to-point optical links. The initial value of the TTL field is 32. The maximum possible value of the TTL field when R receives the datagram is _______.
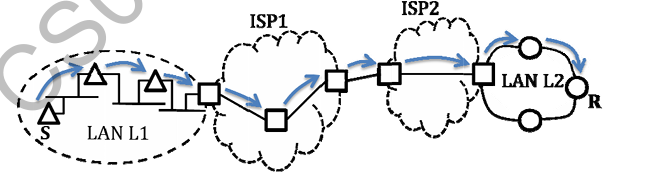
Ques 12 GATE 2014 SET-2
Consider the store and forward packet switched network given below. Assume that the bandwidth of each link is 106 bytes/sec. A user on host A sends a file of size 103 bytes to host B through routers R1 and R2 in three different ways. In the first case a single packet containing the complete file is transmitted from A to B. In the second case, the file is split into 10 equal parts, and these packets are transmitted from A to B. In the third case, the file is split into 20 equal parts and these packets are sent from A to B. Each packet contains 100 bytes of header information along with the user data. Consider only transmission time and ignore processing, queuing and propagation delays. Also assume that there are no errors during transmission. Let T1, T2 and T3 be the times taken to transmit the file in the first, second and third case respectively. Which one of the following is CORRECT?

Ques 13 GATE 2014 SET-2
An IP machine Q has a path to another IP machine H via three IP routers R1, R2, and R3.
Q-R1-R2-R3-H
H acts as an HTTP server, and Q connects to H via HTTP and downloads a file. Session layer encryption is used, with DES as the shared key encryption protocol. Consider the following four pieces of information:
[I1] The URL of the file downloaded by Q
[I2] The TCP port numbers at Q and H
[I3] The IP addresses of Q and H
[I4] The link layer addresses of Q and H
Which of I1, I2, I3, and I4 can an intruder learn through sniffing at R2 alone?

Total Unique Visitors